The protection of application programming interfaces is a critical concern. That’s why finding effective ways to mitigate the top API security risks becomes indispensable.
Updated 24 April 2024

CTO at Appventurez
APIs, or application programming interfaces, have become an essential part of modern software development. Their role in the functioning of an application is imperative — enabling different systems to communicate and share data with each other.
The ever-rising urge to deploy applications faster has further increased the need for APIs. Companies from diverse industries collaborate with a professional software development company to develop and integrate APIs for intuitive solutions. However, APIs exchange crucial data, becoming a soft target for intruders and hackers to access sensitive information.
Therefore, businesses need to have an understanding of the major API security risks and the proactive ways to mitigate them. This informational piece will discuss the top API security threats and suggest related solutions to secure them from cyber attackers.
In general terms, API security can be defined as the process of protecting APIs from malicious attacks. The process focuses on developing an API security strategy, allowing only authorized access to the core systems where API functions.
Developers implement such strategies and employ tools to tackle API security risks, ensuring complete protection of the backend system.
Since API works at the backend, it carries sensitive data including authorization and authentication tokens, input validation, and encryption keys. Due to this, they become highly prone to API security risks, such as bot attacks, malicious injections, and access violations.
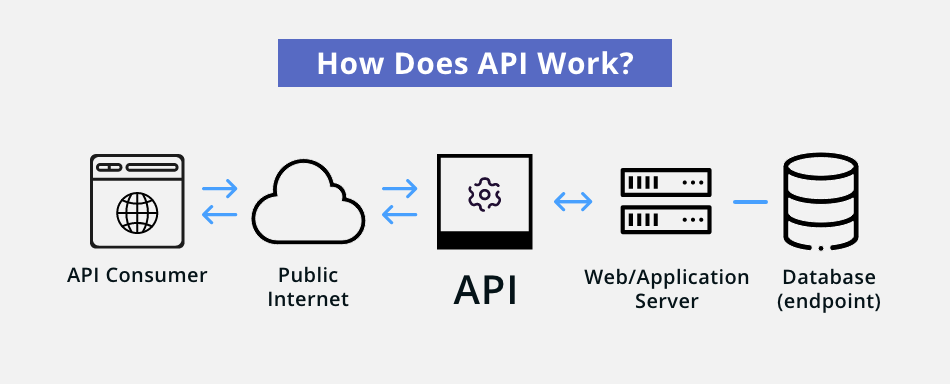
If hackers successfully execute an API attack, they can extract crucial datasets, steal users’ private information, and disrupt app services. That’s why development teams need to keep an eye on the API surface. They must incorporate an API risk management system to constantly monitor APIs and their usage so that API threats can be detected and mitigated timely.
API security challenges have significantly increased in the past few years. More than 41% of organizations have experienced some kind of API security breach in the last year alone. In fact, a survey reported that security incidents in application programming interfaces have increased by 681% in 2022, compared to a 321% increase in total API traffic.

The above illustration depicts which API security issues pose the greatest risk to organizations. All these stats and facts show how vulnerable application programming interfaces have become. Now, let’s explore the prominent API security risks and the reliable ways to combat them.
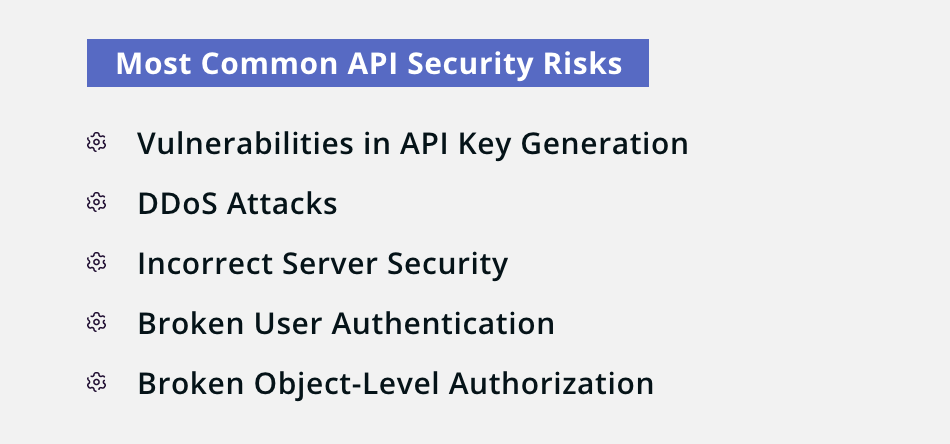
From building to implementation, API development is a complex process. Generally, APIs are secured with the help of JSON Web Tokens (JWTs) or API keys. It enables the security tools to detect any abnormal behavior in the system, blocking the keys and securing the APIs.
However, hackers are capable of outsmarting this approach — deriving and utilizing an enormous pool of API keys from users themselves. It’s similar to how cyber attackers leverage multiple IP addresses to surpass DDoS security.
The straightforward way to tackle these API security risks is to enable users to sign up manually for the service and then generate the keys. To rectify the issue of bot traffic, API security management methods like 2-F authentication and Captchas can be implemented.
One of the most notable API security risks includes Distributed denial-of-service (DDoS) attacks. These API risks overwhelm a network or server with massive traffic, disrupting the targeted traffic. Generally, hackers carry out these attacks remotely with a network of compromised systems or servers, also known as botnets.
Individual bots from a botnet send requests to the targeted victim’s API systems, overwhelming their server and turning ‘denial-of-service’. When it comes to API products, combating DDoS attacks is more challenging than other API security vulnerabilities as segregating bot traffic from genuine ones is cumbersome. These types of attacks often occur in the case of eCommerce APIs.
Finding a solution to these API security risks lies within the API system itself. Whenever access is requested to the web app, one will need an API key. So, whenever you receive a request without an API key, you can immediately reject it.
Non-HTTPS traffic and misconfigured SSL certificates can lead to easy data leaks. This is because when a user accidentally issues a non-HTTPS request from a web app, they expose their API key.
Simply put, without HTTPS protocols and SSL certificates, your APIs are no longer encrypted or secured. As a result, attackers can pose numerous API threats, leading to data compromise.
One of the notable API key security best practices in this case is regularly testing the SSL implementation with the help of an SSL test tool. Apart from this, use the load balancer to block all the non-HTTPS requests.
Broken user authentication is a kind of API security vulnerability in which attackers impersonate users to gain access to an application or website. This area of API security risks is specifically relegated to credential and session management where issues in security practices can help attackers to imitate genuine users.
There are several ways in which attackers can exploit broken user authentication. Some of them include:
To mitigate broken user authentication attacks, multi-factor authentication (MFA) can be implemented. Besides, make sure to use strong cryptographic practices for storing and transferring data to be authenticated.
Broken object-level authorization (BOLA) is a kind of API risk in which attackers send requests for data objects that should be protected with authorization controls. BOLA is also known as an insecure direct object reference (IDOR) attack that provides attackers access to resources that weren’t authorized earlier.
One needs to create a proper access control system to ensure that only authorized users can access specific data. Also, specify user roles and integrate token-based authentication.
As already mentioned, APIs process and transmit sensitive information, the loss of which can lead to serious business issues. Below are some of the critical impacts of API risks to your businesses.

Different types of security risks to organization APIs can cause outages and slowdowns of the operational system. These risks include DDoS attacks, injection attacks, etc, severely impacting the user experience and customer retention.
When any kind of API security vulnerabilities hit businesses, they can lead to significant data breaches. Overcoming these breaches — from regaining the customers’ trust to correcting the security flaws — rebuilding the API structure can be costly.
Today, almost every country creates and follows a data protection framework based on which they levy a heavy fine on businesses that fail to protect user data. API security risks can considerably lead to data breaches, subsequently posing legal challenges to businesses.
APIs play a critical role in transforming your business and elevating it digitally. In that respect, it is crucial to instill an API threat protection system to secure your data-intensive application programming interfaces. Below are some of the benefits of ensuring mobile API security.

Data is a valuable asset, and API security risks can lead to severe damage to the data-backed infrastructure of your organization. A robust API architecture stands firm as a barrier to potential data breaches, ensuring safety for both user and business information.
Strong web and mobile API security is crucial for maintaining services provided by businesses and ensuring seamless deliveries without any kind of disruptions.
A robust application programming interface security framework provides a proactive approach to data protection while complying with the existing legal regulations.
When you ensure that your application programming interfaces are well protected from API security threats, a significant amount of data transmission facilitated by them will be safe, too. It not only promotes data security but also builds users’ trust and confidence.
With more businesses focusing on shifting from monolithic systems to microservices, the types of security risks to organizations will also extend. Consequently, APIs will become more vulnerable than ever.
Due to this, it becomes crucial to leverage the best practices to secure APIs, and in turn, the data they transmit. For this, it becomes crucial to consult with an experienced mobile app development company that ensures keeping your software solutions away from API security risks. Appventurez is that mobile application development partner for you!
Appventurez powers and protects your app solutions. Our team of expert developers, QA testers, and project managers makes sure to build, deliver, and secure your applications and associated APIs. No matter how complicated your software application is, our custom-made mobile API security strategy will ensure keeping it safe and running smoothly.
Q. What is API in cyber security?
In the context of cyber security, the role of application programming interfaces and their security is essential. APIs carry sensitive information about the users and businesses which can become the central point of vulnerabilities.
Q. How secure is the API in the current landscape?
Whenever a user tries to make an API request, the server checks for the API key. If the key is lost or stolen, the intruder can use it to impersonate an authorized user and pose several API security risks.
Q. What are some popular API key security best practices?
Some of the most common and widely used API key security best practices include restricting your API keys, removing unused keys, checking the usage of your keys, and using static web APIs to protect your app.


Elevate your journey and empower your choices with our insightful guidance.

CTO at Appventurez
CTO and Co-Founder at Appventurez, Sitaram Sharma has 10+ years of experience in providing world-class digital solutions. As a CTO, he brought his expertise ranging from product enhancements to advanced technological integrations, while focusing on the consistent growth of the team.
You’re just one step away from turning your idea into a global product.
Everything begins with a simple conversation.