In the last few decades, mobile devices have become a basic necessity for everyone’s lives and the biggest reason is mobile applications. Whether it’s about money transactions and ticket booking to online shopping and checking emails, mobile apps are a boon of people’s lives. Mobile applications are usually accessible through online app distributors such as […]
Updated 21 February 2024

Global Delivery Head at Appventurez
In the last few decades, mobile devices have become a basic necessity for everyone’s lives and the biggest reason is mobile applications. Whether it’s about money transactions and ticket booking to online shopping and checking emails, mobile apps are a boon of people’s lives. Mobile applications are usually accessible through online app distributors such as Google Play Store, Apple App Store, and Window Store. Many companies have also used different types of applications to increase employee productivity while associating themselves with a younger and more connected workforce.
But do you know, along with the ever-growing popularity of mobile apps, the security of apps is becoming so low due to the increasing number of mobile app security threats. So, many hackers are waiting for a chance to steal valuable user information such as credit cards and bank details. According to a report, the top 100 paid Android apps on Google Play Store have been hacked and more than 56% of the top paid iOS apps have been hacked.
So, the need for mobile app security has become the hottest topic for the mobile industry.
Mobile app security is the practice of protecting high-value mobile apps and your digital identity from fraudulent attacks in all its forms. These attacks include reverse engineering, malware, keyloggers and tampering, and other forms of interference. In today’s world, mobile app security has become equally essential as a breach in mobile app security threats not only gives hackers access to the user’s personal life in real-time but also reveals data like their current location, banking information, and personal details.
Mobile apps are a vital part of a business’s online presence and many businesses depend on applications to connect with users from around the world. All popular mobile platforms provide security controls designed to help android developers and iOS developers build secure apps for both platforms.
Beyond an increasing rate of mobile fraud, there are many reasons that financial institutions should take mobile application security seriously and commit to developing a comprehensive strategy. Consumers need to be careful about the information they reveal and the data they download when browsing the internet, but as a business professional, you should be attentive as well. Mobile apps may be forward in the permissions they ask for. Why might a weather application need access to your camera or microphone? And might an attacker find a vulnerability in that application that grants them access to the camera or microphone to conduct industrial surveillance?
Consumers are often dependent and trust companies to test their apps for security before making them available. But IBM’s studies revealed shocking facts shown in the figure below.

The above numbers provide enough motivation for hackers to use security loopholes in mobile apps and hackers try to leverage any or all of the following things from unsecured codes:
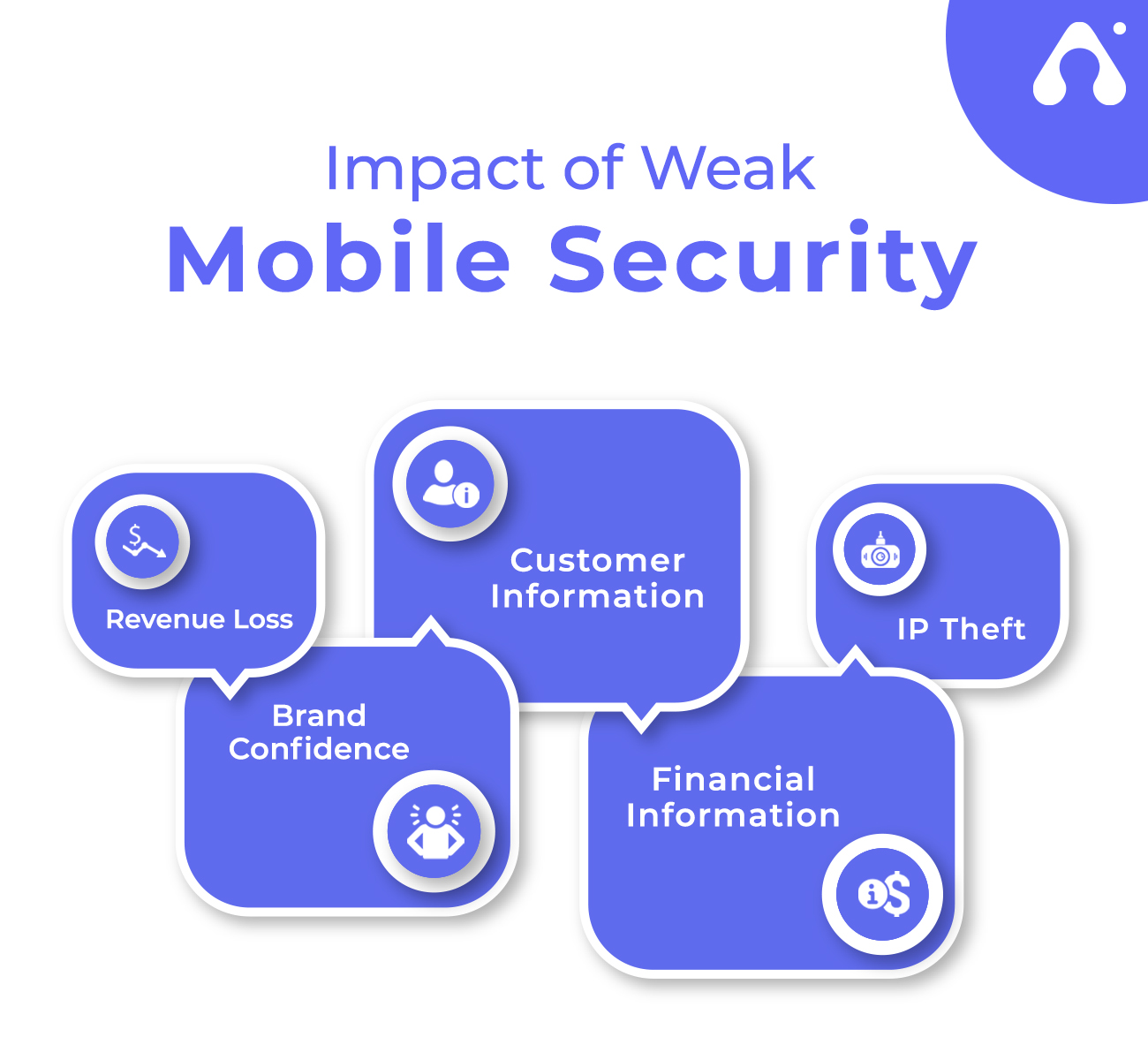
Hackers get login credentials of any website including email, banking, and social networking websites. A notorious example of this category is Anubis Banking Trojan. It enters the user’s device by downloading compromised applications in which some are hosted on the Android’s official app stores. In May 2019, Whatsapp admitted that its application was suspected to be spyware from an Israeli firm NSO group that could infect a mobile device simply by calling a user on WhatsApp from an unknown number. The users’ devices could be compromised even if the user didn’t accept the call. After infected devices, the spyware could send all data including contact lists, GPS information, and media files from their devices to the hacker’s server.
Hackers can gain financial information including bank account numbers, credit, and debit card details to make bank transactions, especially in cases where a one-time password is not essential. Researchers from Kaspersky discovered a new version of the banking Trojan called Ginp which could steal user credentials and credit card information from a user’s device. This Trojan’s ability to take control of the device’s SMS feature allows it to manipulate banking functions.
It is possible to access apps’ premium features, especially in utility and gaming applications which are a source of revenue for the owner of the app. In 2016, the mobile security company Bluebox revealed how hackers were able to access the premium features of popular apps Hulu and Tinder by exploiting security holes in them and causing losses to their owners. At that time, Hulu’s monthly subscriptions were selling at $7.99 a month for its OTT streaming service.
Apart from losing important user data, the loss can come in the form of both misuses of user information as well as lawsuits from affected parties. The positive part of undertaking security drills is that customers stay loyal and trust the brand while the negative is the loss of customers’ confidence forever. The rationale for android and iOS app development should rightfully consider their business’s aspect.
Instead of serving as anti-viruses or transmitting data securely over the internet, mobile apps focus on a smooth interface and offer the best functionality to users. While an antivirus app installation may secure the devices from different threats, it can’t protect against weak passwords or a poorly designed app.
Many common security failures are documented by industry experts under the curve of the Open Web Application Security Project (OWASP) for mobile app development companies’ reference. Here are some top 10 OWASP mobile in the below-given diagram.
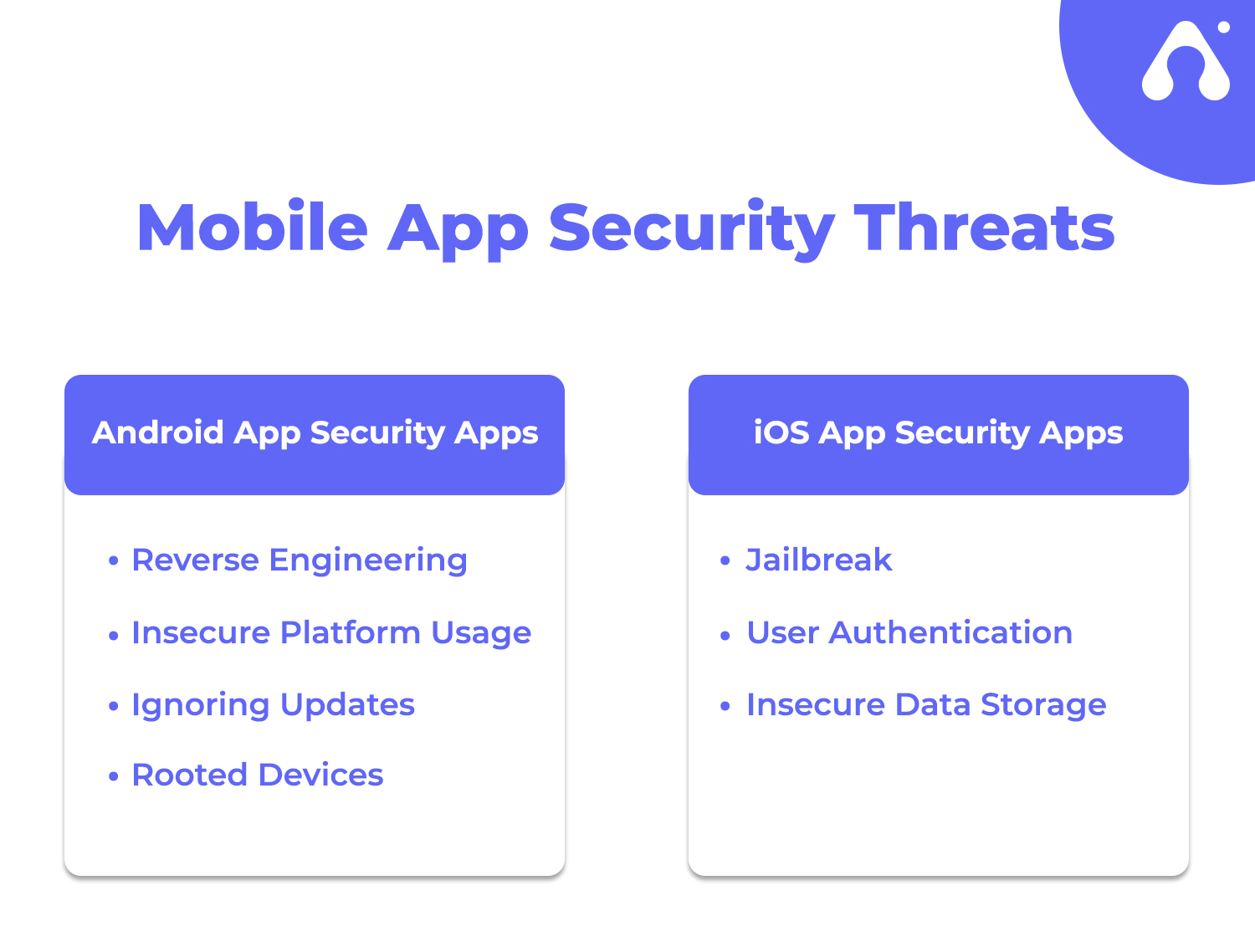
Here, you will read about both Android and iOS applications’ security risks. Let’s first dive into Android app security risks.
Reversing Android apps can easily provide test login credentials, insights into bad design, details about the libraries and classes. It can also provide details about the encryption type used in the application which can help the attacker not only hack one device but multiple devices as well by using the same decryption method.
Hackers search on Android devices to get BroadcastReceiver instances which are meant for legitimate apps. On the other hand, developers prefer to ignore the use of LocalBroadcastManager to send and receive messages for legal applications, thus creating a security failure.
Many Android app developers don’t update their apps regularly or pay to the operating system patches issued by Android which results in a lack of protection against newly found vulnerabilities. Updates cover the latest security covers and avoiding the same can expose apps to the latest security risks.
Unlike Android, the iOS operating system strictly imposes security features. It is a closed OS which means apps can’t communicate with other apps or directly access other applications’ data. iOS apps are built-in native Objective C language with tools like Xcode. It is based on the same RAM version of the XNU kernel as that of OSX which is used in Apple’s laptops and Mac computers.
Jailbreaking is mostly used in the context of Apple devices. This term includes finding an exploit in the Kernel that lets users run unsigned code on mobile devices. Jailbreaking is secured which means whenever you reboot your phone, the code will remain on your phone even after a reboot.
iOS claims that they are secure as they use a processor separate from other operating systems. This processor is also known as Secure Enclave which runs on a dedicated microkernel. And even iOS app development offers device-level security through Face ID and Touch ID. However, hackers have proved that these security features can be compromised with a device called GrayKey. This device allows investigators to unlock a locked iPhone without any user’s permission. When application developers use touch security devices to protect their data or services within the application, they are also exposed to this type of vulnerability.
Many applications store data in SQL databases, cookies, binary data, or even as common text. These storage locations can be accessed by hackers when the OS, framework, or compiler is vulnerable. When hackers gain access to the database, they change the application and gather details on their machines. Security experts have also observed that insecure data storage is one of the most common vulnerabilities in iOS devices which hackers exploit to steal passwords, financial information, and personal users’ data.

Here are 8 step to enhance mobile app security
The secret language between mobile apps is called API (Application Programming Interface) that requires great security as it is the most susceptible to getting attacked. To protect your mobile applications from hackers, you need to make APIs more secure by following these ways.
Another factor that contributes to a breach of the environment is unsecured network connections that lead to unauthorized access by other cloud services. Let’s take a look at the different ways that we can protect our phones from being hacked due to poor network connection issues.
Data stored by the user in the smart device is more vulnerable to attacks. Encrypting complete data might affect user experience, so it is advisable to encrypt only sensitive information stored by the user, for example, financial details. To encrypt the mobile database, you need to follow methods:
Creating confusing codes is the best way to protect your mobile applications from hackers as it may be difficult for hackers to read the obscure codes. Sirius, DashO, and TotalCode are examples of obfuscation tools that you can use for ensuring that the hackers can’t reverse engineer a software program.
Some ways to build a unique source code:
Before developing a mobile app, you need to create a checklist of mobile app security threats and weak spots. Here is a list of some common weak spots below:
Before launching any app in the market, checking data security is one of the most important processes during the testing process. If there are security breaches present, you need to perform a beta-testing on the application to find out the security breaches.
Here are some tips to help in testing the security of your app:
You can use security tools such as android Debug Bridge, iPad File Explorer, QARK, Clang Static Analyzer, Smart Phone Dumb Apps, and OWA SP Zed Attack Proxy Project for ensuring the proper functionality of your application.
During working on a mobile app, make sure you use the latest version of the libraries to avoid any breach of security. While many essential vulnerabilities in third-party libraries are disclosed as CVEs (Common Vulnerabilities and Exposures), it is disconnecting to note that the apps that use themes are not updated promptly.
Mobile application development must be in sync with the corporate policies of the company’s IT administrators. Apart from this, it should comply with the Google Play Store and Apple Store. It is possible to reduce the attack of your app by using secure frameworks.
By doing these 8 things properly, your mobile app security issues can be prevented. Security for apps can never be at 100%, it is not a negative statement. In turn, this means constant monitoring and timely testing with error fixing is the best way to ensure maximum safety of your application. If you want to know mobile application security tools and strategies, you can get in touch with Appventurez for the best solution.


Elevate your journey and empower your choices with our insightful guidance.

Global Delivery Head at Appventurez
Ashish governs the process of software delivery operations. He ensures the end product attains the highest remarks in qualitative analysis and is streamlined to the clientele’s objectives. He has over a decade of experience as an iOS developer and teams mentorship.
You’re just one step away from turning your idea into a global product.
Everything begins with a simple conversation.